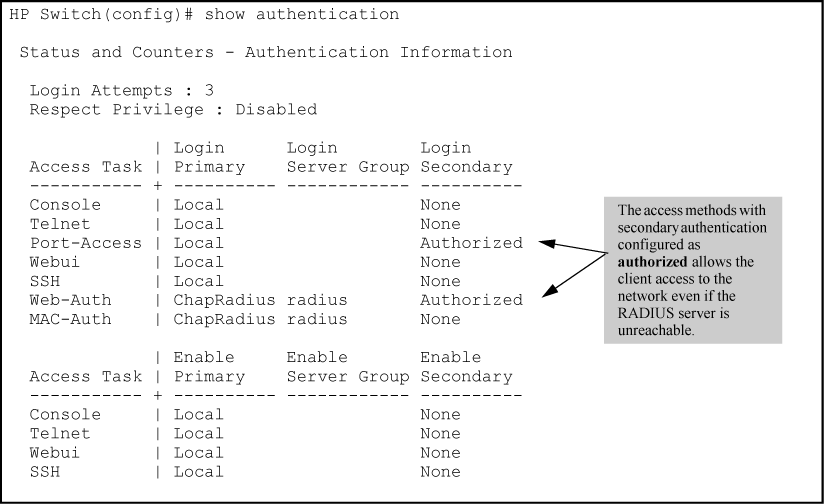
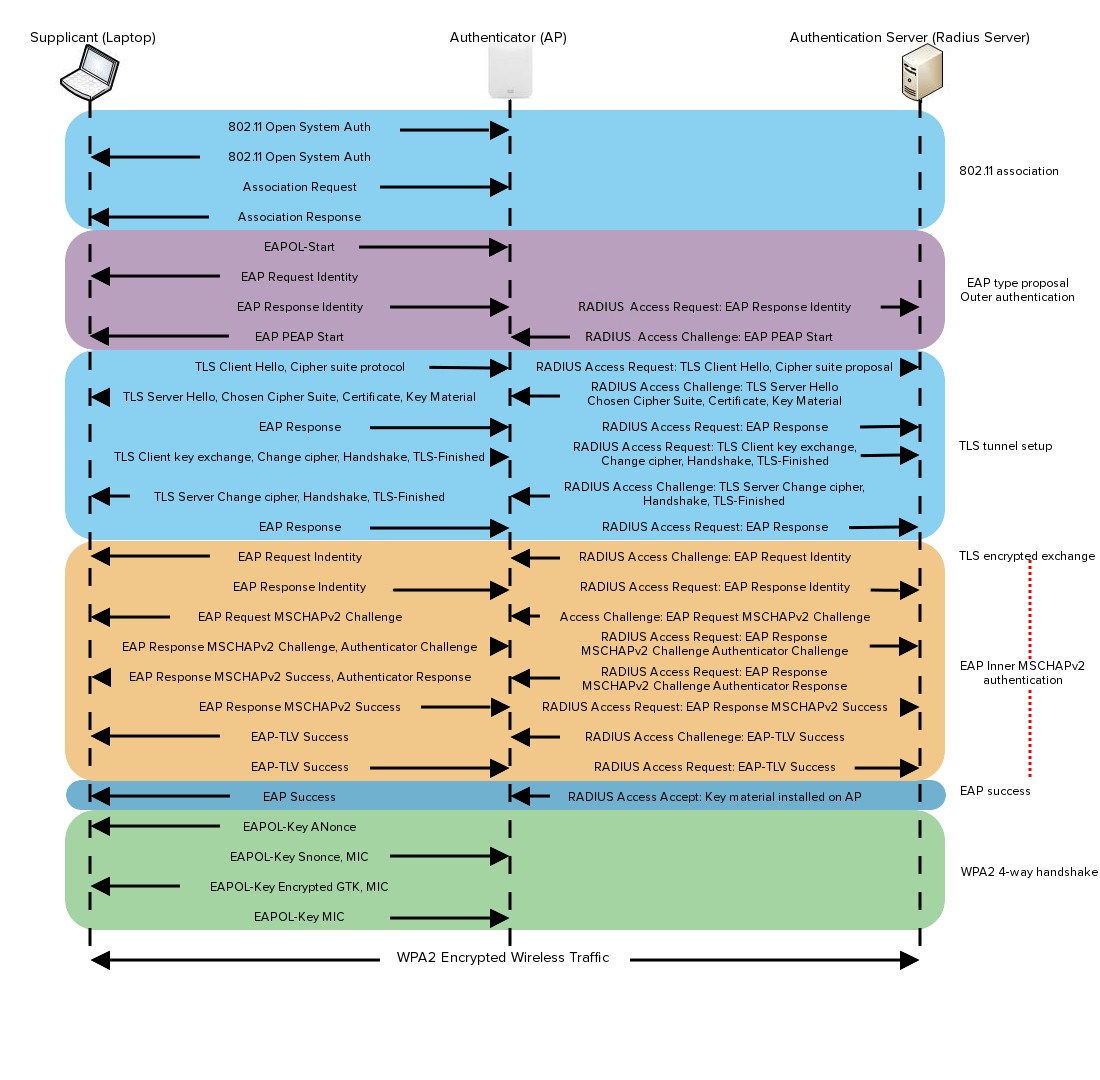
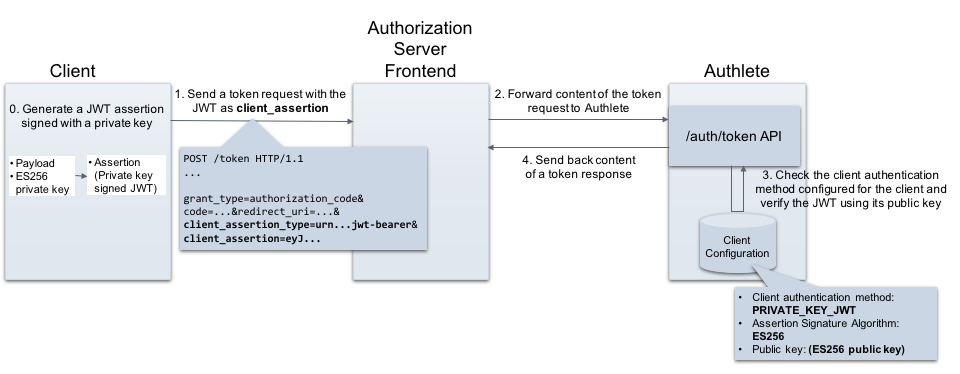
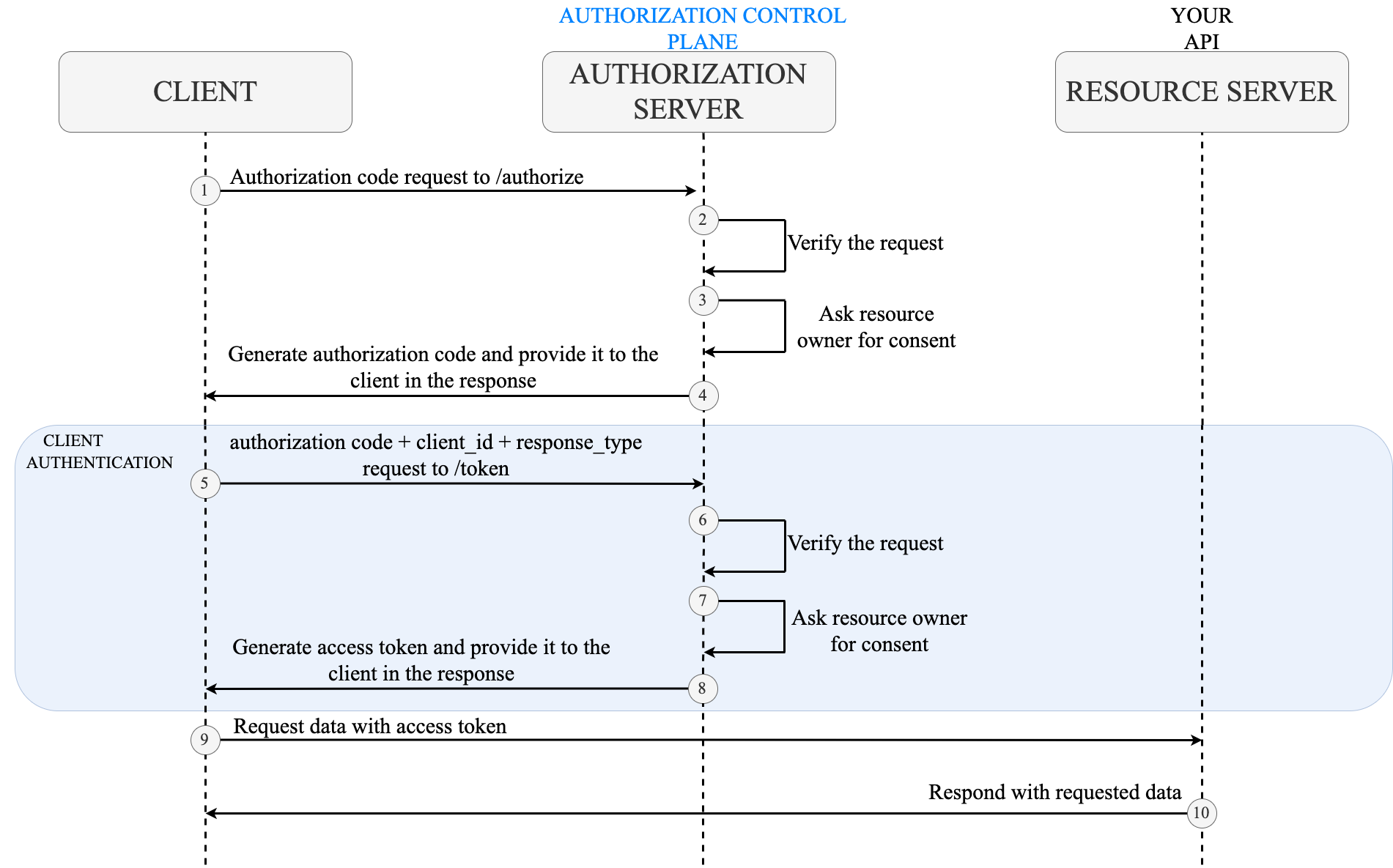
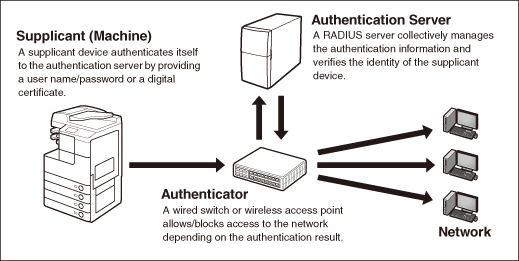
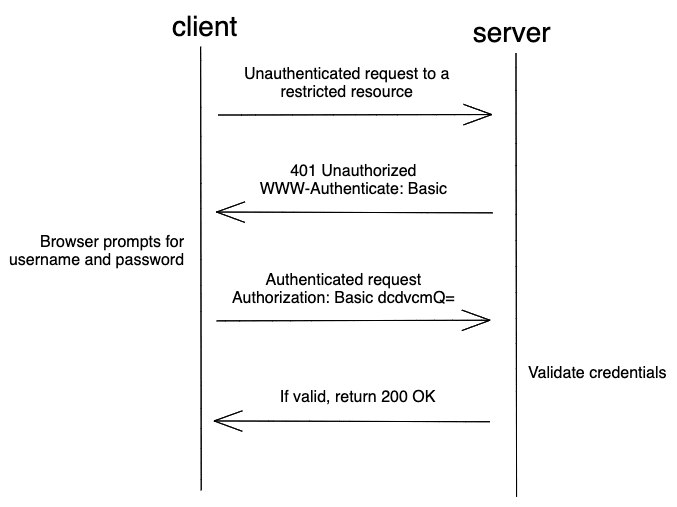
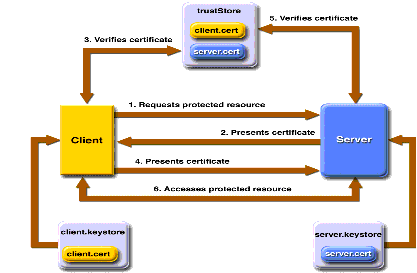
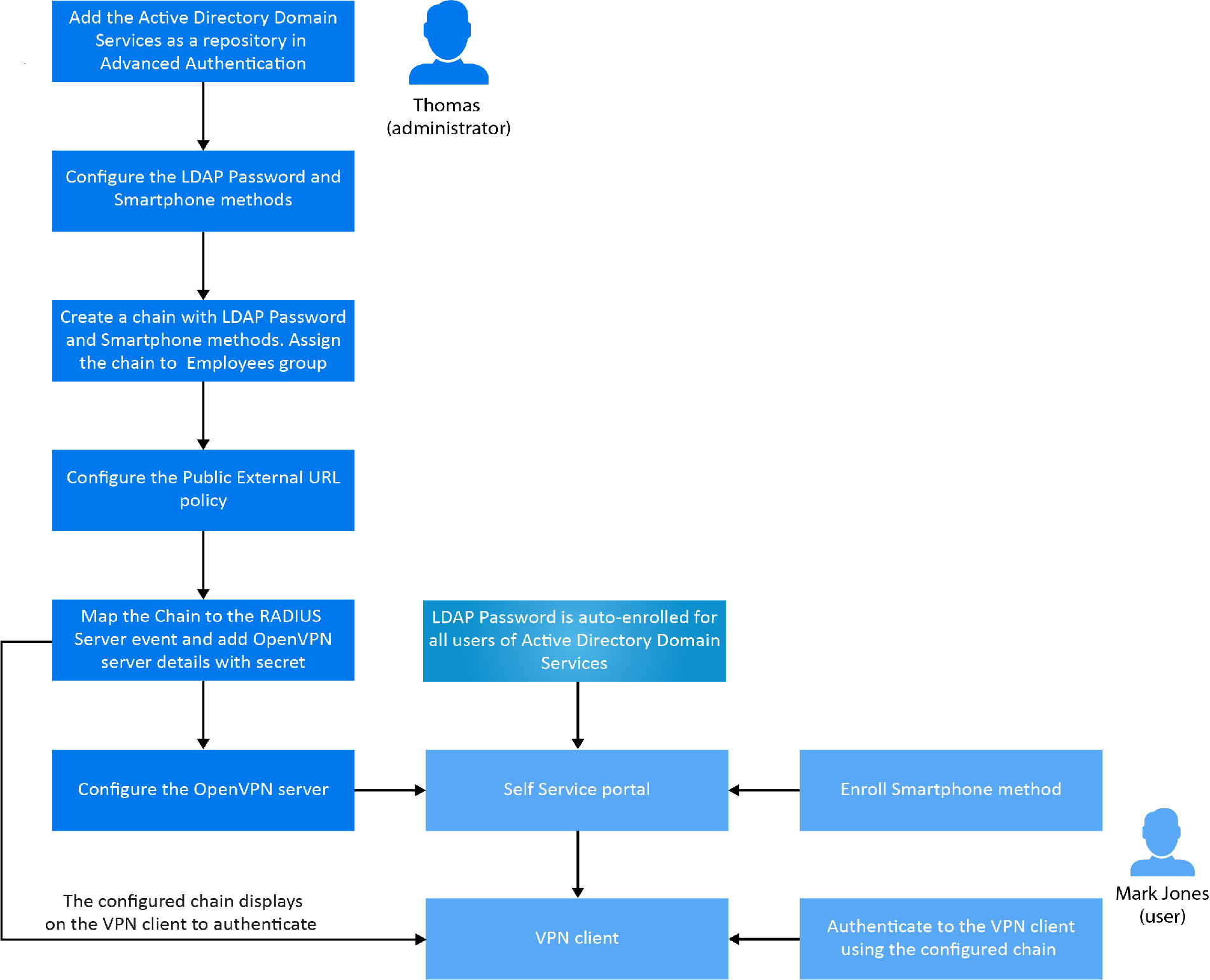
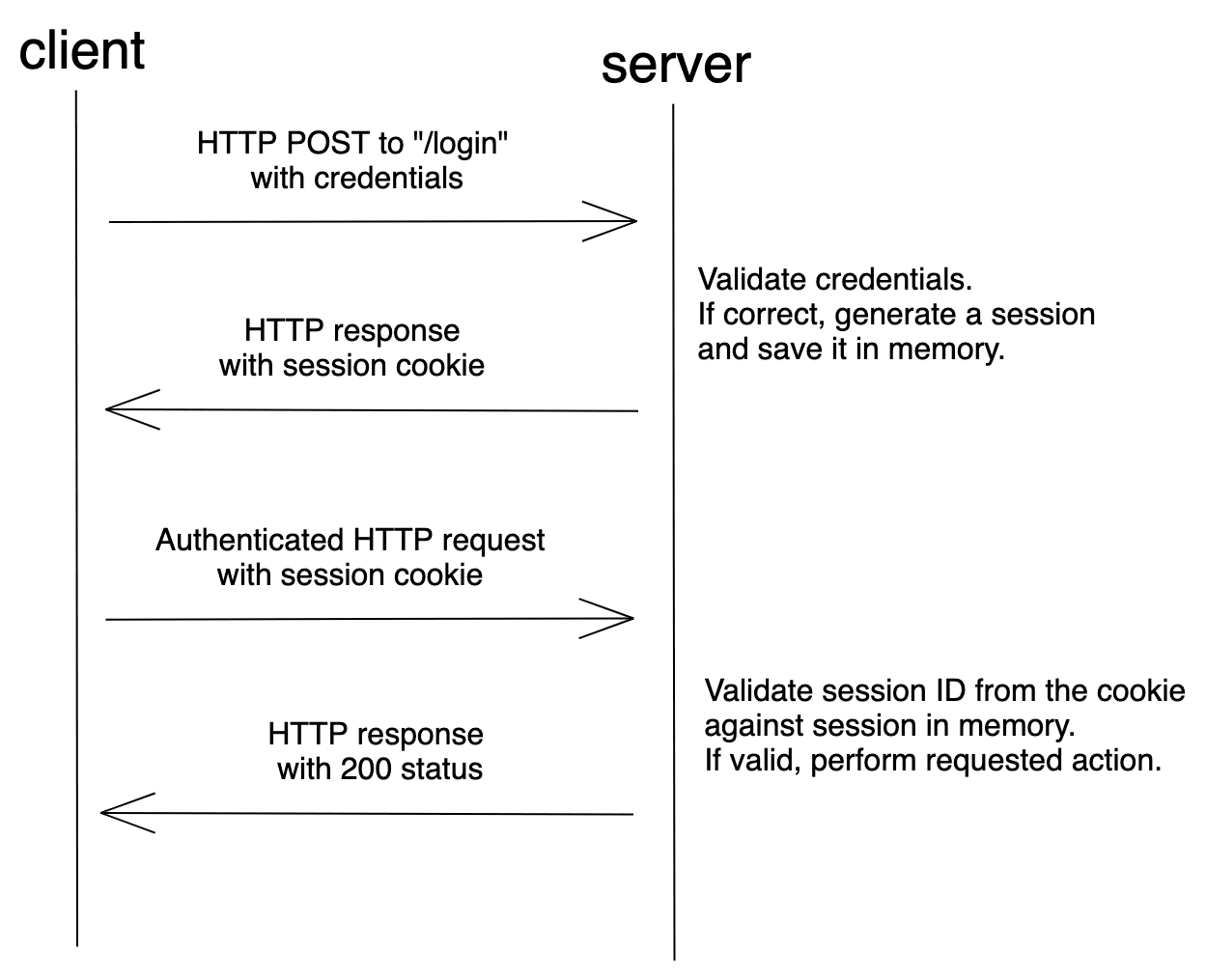
OAuth 2.0 Client Authentication. This article explains “OAuth 2.0 client… | by Takahiko Kawasaki | Medium
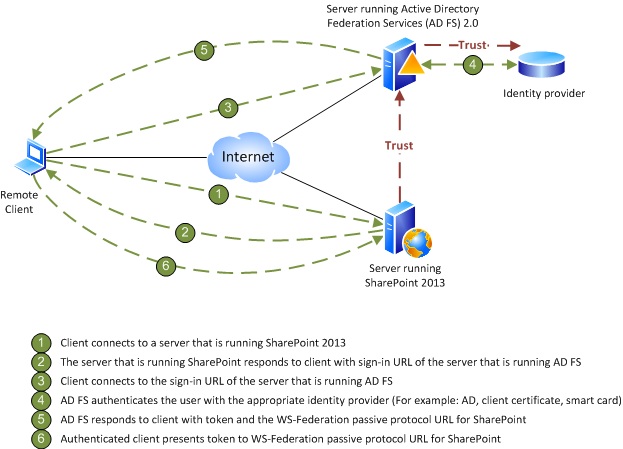
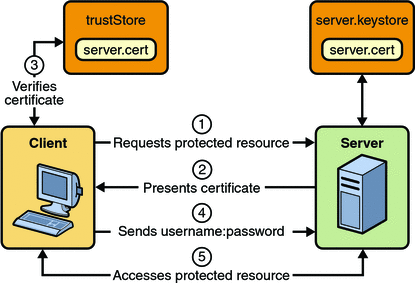
Configure client certificate authentication for SharePoint Server - SharePoint Server | Microsoft Docs
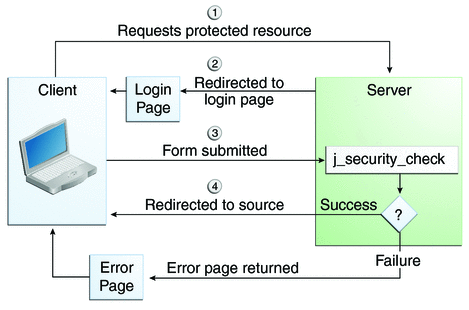
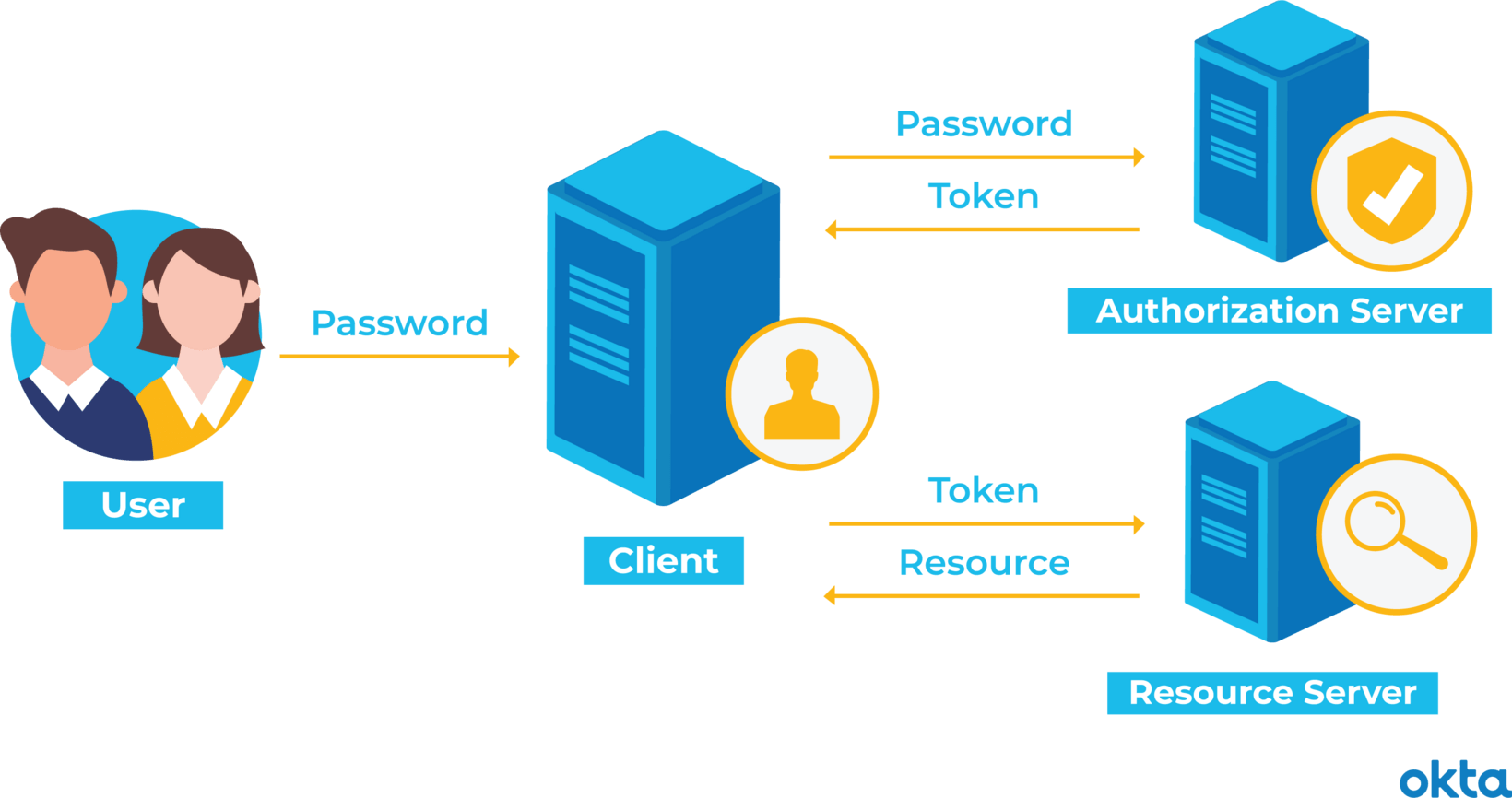
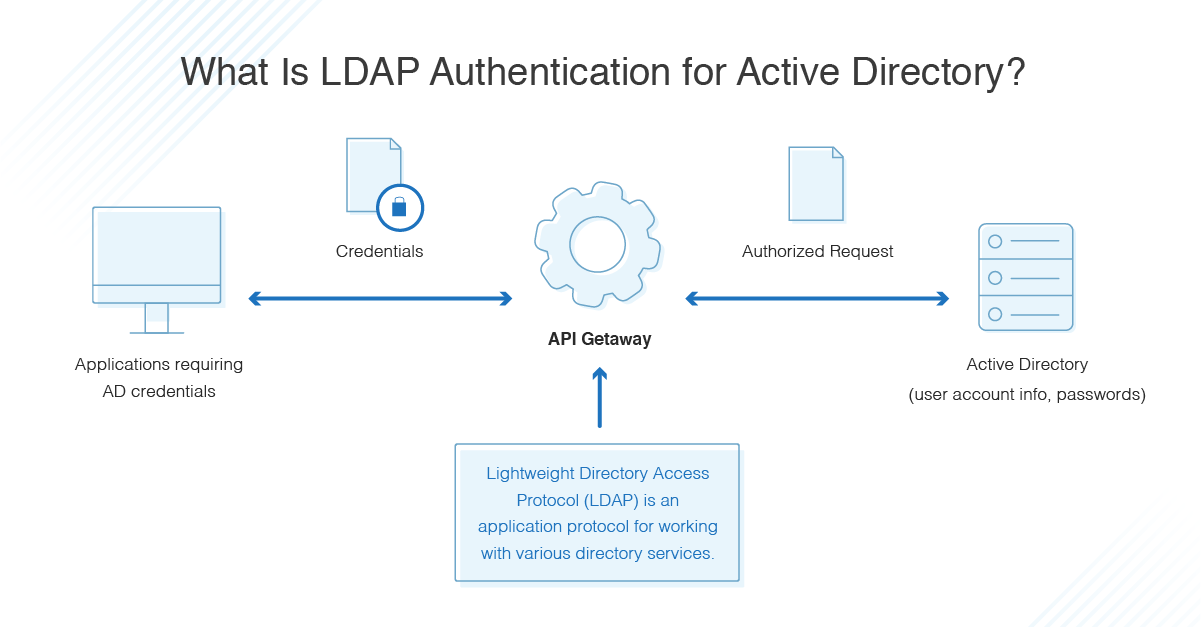
How Do You Authenticate, Mate?. A definitive guide to authentication… | by Ahmed shamim hassan | Better Programming